Solutions
To meet your needs
Next-Gen Computing
Cloud Infrastructure Management & Automation (CIMA)
Enterprise Linux Provisioning, Optimization & Hardening
Cloud & Application Readiness Services (CARS)
Web Application Readiness & Optimization Services (WAROS)
Core Infrastructure (CI)
Automate Deployment and Management of infra component

Cyber Security
Cyber Security Health Check
Provides a holistic view of your cyber security risks and areas that require attention
Vulnerability Assessment and Penetration Testing
Helps you improve efficiency of security operations by risk-based vulnerability management with automated penetration testing solution.
SIEM & End Point Protection
Equips security teams to prevent, detect, and respond to threats at cloud speed and scale

Data & AI
Data & AI Platforms
HPE Ezmeral
Neo4j
Cloudera
KNIME
PostgreSQL (CITUS)
Data Engineering & AI Services
PySpark
Neo4j Cypher
Airflow
Superset
KNIME
Data & AI Products (Solutions)
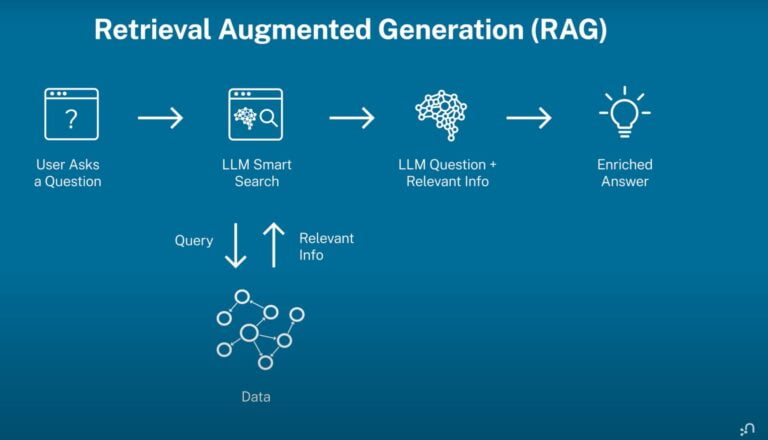
AI Assisted Knowledge Base (Retrieval Augmented Generation)
Fraud Detection & Management (Applying Graph Database)
Digital Twin (Backend & Data)
Avoid Vendor Lock-In By using full Open Source solution with Enterprise Grade Support SLA from ABYRES
Why us
Enterprise Open Source Provider
We are a pure-play Open Source & Open Computing company. Operated since 1997, we have established our position as the Trusted Adviser and the Open Source Technology Partner with large Enterprise and Public Sector clients. Coupled with ABYRES’s well-experienced and dedicated staff, we provide right solutions at the right price, justifying our customer’s IT investments and deployments.
A decade of proven Open Source Computing expertise.
Serving a thriving community of satisfied customers.
A dedicated team of Open Source Computing expert at your service.
Guided by integrity, trust, and client-centricity, our values drive everything we do.
Integrity
Uphold high ethical standards and act with honesty, transparency, and professionalism in all your interactions.
Trust and Confidentiality
Understand the importance of trust and confidentiality in your client relationships.
Objectivity
Provide unbiased advice that is based on thorough analysis, research, and a comprehensive understanding of your clients' financial situations.
Expertise
Stay up-to-date with industry trends, regulations, and best practices to offer informed advice to your clients.
Long-Term Relationships
Build long-term relationships with your clients based on trust, open communication, and mutual respect.
Accountability
Monitor progress, review strategies, and make adjustments as needed to help clients stay on track towards their financial goals.
Success Stories
Next-gen computing
Server Virtualization
Server Virtualization Platform: Help customer reduce cost by moving from Enterprise Open-Source to community version. Successfully run mission critical workload application for federal agencies and state government.
System Optimization
Web Application Readiness and Optimization This process involves ensuring that the web application is fully prepared for deployment, including comprehensive testing, performance tuning, and security checks.
Infrastructure Monitoring
Custom built Telemetry for Infra Monitoring Continuously track and analyze system performance metrics, resource utilization rates, and error logs to facilitate comprehensive troubleshooting and ensure system reliability.
Database Implementation & Support
Highly Available Database Evolve the conventional standalone database into a clustered database architecture to manage mission-critical workloads, while ensuring the highest levels of performance and availability.
Cyber Security
VAPT
Assess Platform and Application (VAPT) Identify vulnerabilities and weaknesses to prevent exploitation by actual cybercriminals
Health Check
Cyber Security Health Check Conduct a Cyber Security Health Assessment to identify potential threats within a specific organization
Security Operation Center
SOC Platform Implementation Create a tailored solution encompassing both hardware and software, appropriately scaled for a Security Operations Center (SOC) to monitor and respond to thousands of endpoints
Health Check
Cyber Security Health Check Conduct a Cyber Security Health Assessment to identify potential threats within a specific organization / SMEs.
Data & AI
Data Lake & Data Engineering Consulting
Malaysia’s 1st National Big Data Pilot Project Architectural consulting & implementation of data lake for pilot projects
Data Lake Enterprise
Data Lake for Telco Revenue Assurance Centralized data lake, keeps copies of data from multiple endpoints with historical snapshots
Data Application Development
Malware Removal Coordination Engine Application development of malware detection and removal platform, powered by Big Data technologies
Data Engineering Consulting
Consulting & Training for HADOOP & ElasticSearch To enable their developers, and guide them in implementing solutions on Hadoop and ElasticSearch
Get started
Schedule your personalized consultation today

We
are
better
together.
Drop your contact details into the form, and we’ll reach out to you!